The hardest part about TCPA in 2025 isn’t knowing the rules. It’s building a dialing system that can scale hard and prove, in writing, that every call respected consent, channel, and timing. One mistake and you’re staring at complaints, chargebacks, and class-action language. But if you overreact, you end up with reps baby-dialing from spreadsheets while competitors run compliant, high-velocity engines. This guide is for teams that want a “TCPA-proof” stack in practice: consent-first architecture, dialer logic that can defend itself, and AI that shrinks risk instead of inflating it.
1. “TCPA-Proof” in 2025-2026 Means Architecture, Not Just Legal Disclaimers
If your answer to TCPA is “we added a checkbox and a footer line,” you’re already behind. Regulators and plaintiffs don’t care what your landing page said; they care about what actually happened to each number in your dialer. A genuinely TCPA-safe system treats consent, channel, and purpose as data objects that control routing and pacing, not as fine print. That’s why the most mature outbound and CX teams pair legal guidance with dialer logic similar to the patterns in modern auto-dialer compliance frameworks.
In practice, that means every outbound decision is explainable. Why was this number dialed? What kind of consent did you have? Which dialer mode was used? What time zone was assumed? Where is the evidence stored? TCPA-proof in 2025 isn’t about never being questioned; it’s about being able to answer those questions instantly, with logs, instead of scrambling through CSV exports and Slack threads.
2. Map Your Risk Surface Before You Touch the Dialer
Before you choose “predictive vs progressive vs power,” map what TCPA actually touches in your business. It’s not just your sales floor; it’s every triggered call, reminder, and outreach campaign. Start by listing all the ways your systems originate calls: manual outbound, auto dialer campaigns, IVR callbacks, payment reminders, collections, renewals. Then break down list sources and consent flows. Are you bringing in data from forms, partners, events, or imported spreadsheets? Each path has different risk and documentation expectations, which is why mature shops align their mapping work with the same rigor they use in advanced call center metric audits.
Once you’ve mapped flows, classify each campaign: informational vs marketing, warm vs cold, mobile vs landline, domestic vs cross-border. Those labels should live in your systems, not just in someone’s head. They will drive which dialer modes you’re comfortable with, what scripts you permit, and which campaigns get extra compliance review before launch.
| Area | Key Questions | Risk if Ignored |
|---|---|---|
| List source | Where did each contact come from? Form, partner, event, upload? | No traceable origin; hard to prove consent. |
| Consent type | Express written, express, or implied? For what channel? | Wrong consent category applied to campaigns. |
| Campaign purpose | Informational, servicing, collections, or marketing? | Marketing treated as “service,” raising risk. |
| Number type | Mobile, landline, VoIP, unknown? | Autodialing numbers you shouldn’t be touching. |
| Dialer mode | Predictive, progressive, power, or manual? | Over-aggressive pacing, higher abandonment. |
| Time zone | How do you calculate local time for quiet hours? | Calls landing outside allowed windows. |
| DNC handling | Internal and external DNC lists enforced where? | Repeat dialing objectors or listed numbers. |
| Partner data | How do you vet and tag third-party lists? | Liability inherited from upstream sellers. |
| Opt-out logic | How fast do “stop” and verbal opt-outs propagate? | Continued dialing post opt-out. |
| Script library | Which openings and disclosures are allowed? | Inconsistent language across agents and teams. |
| Recording rules | Where is consent to record captured and stored? | Recording without proper notice in some regions. |
| Vendor stack | Which cloud dialers/VOIP carriers are in scope? | Blind spots in contractual responsibilities. |
| AI usage | Where do you use AI for routing, scoring, or outreach? | Opaque decisions without audit trails. |
| Cross-border calls | Which countries and regimes are you reaching? | Overlooked local rules for international campaigns. |
| Evidence storage | Where do consent, call logs, and recordings live? | No defensible audit trail during disputes. |
3. Design a Consent-First Dialing Architecture
Once you’ve mapped the risk, bake it into your architecture. The safest 2025 stacks treat “consent” like a routing object — exactly like language, skill, or segment. Your cloud contact center or VOIP platform should read consent flags and number type before deciding what kind of dialer logic to use, echoing the same “rules first, calls second” mindset used in zero-downtime call system designs. If consent is missing, ambiguous, or withdrawn, the system should refuse to launch that record in high-automation campaigns.
Underneath, you need a VOIP and PBX layer that’s modern enough to enforce rules centrally. Legacy on-prem boxes and ad-hoc SIP trunks make it almost impossible to guarantee behavior across every site and team. That’s why many teams use global-ready setups similar to cloud PBX architectures, where all dialing flows through one policy-aware brain. Once that’s in place, adding or removing campaigns, numbers, or vendors doesn’t mean rewriting compliance logic from scratch.
Finally, build your data model to expect change: new consent language, new quiet hours, new regions. You don’t want to edit ten dialer configs every time legal updates wording. Store rules once; enforce them everywhere. That’s the same scalability principle you see in SIP-to-AI telephony migrations, applied to TCPA instead of just audio quality.
4. Choose Dialer Modes Through a TCPA Lens, Not Just a Revenue Lens
Predictive, progressive, and power dialing are not inherently compliant or non-compliant; they’re just easier or harder to govern. Predictive dialers, for example, are fantastic at mining “dead time” when used inside disciplined playbooks like advanced predictive strategy libraries. But if abandonment limits, list hygiene, and quiet hours are an afterthought, they can become a liability amplifier.
A TCPA-proof outbound program starts from risk posture, then chooses modes. For high-risk segments (uncertain consent, mixed number types), keep automation conservative: progressive or even power with strict caps. For well-documented, high-consent segments, you can safely introduce predictive to squeeze more value from the same headcount, provided you actively monitor abandonment and complaint rates. That’s exactly why leaders compare dialer vendors and pacing controls so closely in evaluations like large-scale auto dialer comparisons.
Whatever mode you run, always decide it per campaign, not per platform. Your collections team, renewals pod, and cold SMB motion may all deserve different defaults inside the same cloud contact center.
5. Build a Stack Where Every Call Is Its Own Piece of Evidence
To be defensible, TCPA programs need more than policies; they need receipts. That starts with your call center platform. Every outbound attempt should generate a record tying together the number, campaign, agent, timestamp, dialer mode, and outcome. These logs should sit alongside CRM context so that if a contact disputes a call, you can show how they entered your system, what they agreed to, and how that consent was honored, similar to how integrations are orchestrated in integration-heavy call center stacks.
Recording and transcription, done correctly, become another layer of protection. With the right announcements and regional policies in place, AI-powered QA can scan calls for required disclosures, opt-out language, and risky deviations from script. When combined with real-time coaching engines like live AI agent assist platforms, your stack doesn’t just find problems after the fact; it helps reps stay inside the rails while the call is happening.
Underneath all of this sits telephony. If you’re still juggling on-prem PBX hardware and ad-hoc trunks, it’s extremely hard to keep policy, routing, and evidence consistent. That’s why many compliance-minded teams move to centralized cloud infrastructures aligned with modern PBX and VOIP redesigns, where there’s one canonical place to apply and audit dialing rules.
6. Operational Playbooks: Scripts, Training, and QA That Actually Reduce Risk
A TCPA-proof dialer with non-TCPA scripts is still a liability. Your agents need clear, versioned openings and disclosures for each campaign type, along with specific language for handling opt-outs, wrong numbers, and “I never gave you permission” objections. Those scripts should live in the same system that runs your dialer so that changes propagate quickly, just like routing or IVR updates do in well-designed cloud contact centers.
Training can’t be a one-time deck. Reps forget; new hires join; products evolve. Build monthly micro-modules focused on a single risk pattern — for example, how to treat reassigned numbers, or what to do when someone references past calls. Then backstop training with AI QA and scorecards that include compliance criteria alongside sales or CX metrics. That’s how forward-leaning teams use AI from cost-reduction toolkits not just to save labor, but to catch and correct risky behaviors at scale.
Finally, treat QA and legal as collaborators, not adversaries. Give QA the tools to tag and escalate potential TCPA issues quickly, and give legal reporting views that make patterns obvious: campaigns, teams, and scripts that generate disproportionate complaints or opt-outs.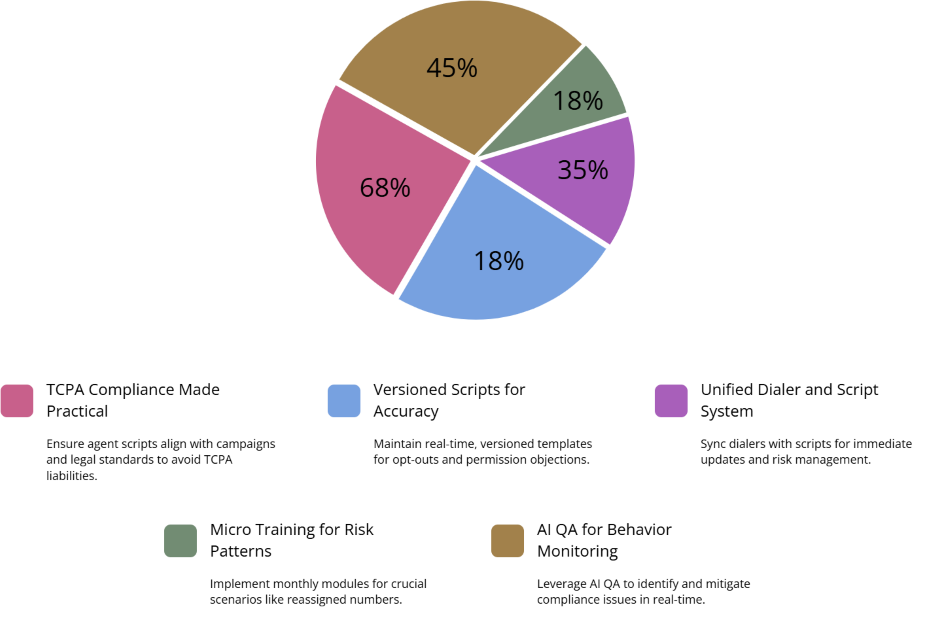
7. 30/60/90-Day Plan to “TCPA-Proof” Your Dialing Without Killing Growth
Days 1–30 — Discover and classify. Inventory every outbound flow, vendor, and list source. Apply the risk checklist above and group campaigns into tiers. In parallel, benchmark your current stack’s capabilities against modern architectures like downtime-free cloud contact centers. Identify which controls (DNC, time windows, consent tags, logs) are missing or scattered.
Days 31–60 — Re-platform and re-design. Where necessary, consolidate telephony and dialing into a single policy-aware platform inspired by the multi-site setups in multi-office VOIP rollouts. Implement centralized DNC, consent, and time-zone logic. Split campaigns by risk, choosing dialer modes accordingly. Stand up AI QA on at least one high-volume campaign so you can begin gathering evidence and patterns quickly.
Days 61–90 — Automate and harden. Layer AI assistance to keep agents inside scripts; refine pacing and modes for high-consent campaigns; and roll out weekly TCPA dashboards. Align your go-to-market “push” projects with this new, safer foundation so sales and CX feel the benefits immediately. Where you see ongoing risk, treat it as a product backlog: small, prioritized fixes instead of once-a-year “compliance panic” meetings. Over time, this is the same mindset that lets teams move from fragile dialers to resilient stacks like those documented in PBX-to-cloud migration guides.
8. FAQ — Scaling Dialers While Staying TCPA-Safe in 2025
Can a predictive dialer ever be “TCPA-safe,” or should we avoid it completely?
Predictive dialers can be part of a TCPA-safe program, but only when they’re wrapped in strict rules, clean data, and constant monitoring. You need abandonment caps, segmentation by consent level, and accurate time-zone handling. Many teams reserve predictive modes for well-documented, high-consent campaigns and keep progressive or power dialing for mixed lists. Think of predictive as an advanced feature you earn after building the foundations described in modern U.S. outbound dialer setups, not as a default switch.
What’s the fastest way to reduce TCPA risk without killing our outbound volume?
Start by centralizing DNC and opt-out logic, then refactor your campaigns by risk. Often you can keep volume nearly flat by shifting high-risk lists into safer dialer modes while leaving high-consent segments in more automated flows. In parallel, roll out AI QA to catch missing disclosures or mishandled objections early, similar to the approaches in AI-augmented dialing environments. You get quick reductions in risk with minimal impact on revenue while you work on deeper architectural changes.
How much of TCPA compliance can we expect from our dialer vendor vs our own team?
Your vendor can provide tools — DNC lists, pacing controls, audit logs, AI QA — but they can’t decide who you call, how you source data, or which scripts you run. The most successful teams treat their platform like the engine described in scalable, compliant call center designs: a powerful but neutral layer. Compliance is shared: your vendor must expose the right controls and evidence; your team must configure and govern them intelligently.
How do AI tools fit into TCPA — do they make things safer or riskier?
AI can create risk if used to spray untested outbound campaigns, but it can dramatically reduce risk when focused on QA, coaching, and anomaly detection. Voice analytics and auto-scoring can review 100% of calls for compliance patterns; real-time assist can remind agents of required disclosures in the moment. This is how forward-looking operations use AI like in live coaching stacks: to prevent issues before they escalate instead of just optimizing for speed.
We already migrated to a cloud telephony platform. Does that mean we’re TCPA-proof?
Cloud telephony and CCaaS are necessary, but not sufficient. Moving from on-prem to cloud gives you better routing, logging, and integration options, similar to the transitions captured in reliability-focused cloud migrations. But TCPA safety still depends on how you tag consent, configure campaigns, train agents, and monitor behavior. Think of cloud as the canvas; the compliance picture is something you still have to paint carefully.
A truly TCPA-proof dialing system doesn’t feel like a legal straitjacket. Done right, it becomes a growth multiplier: your outbound engine can run harder, in more markets, with more automation, precisely because you know where the lines are and you’ve wired your stack not to cross them by accident. That’s the difference between hoping you’re safe and being able to prove it — call by call, campaign by campaign.